
ISO 27001 Information Security Management System
Get Price Quote
Iso/iec 27001 is an information security standard, part of the iso/iec 27000 family of standards, of which the last version was published in 2013, with a few minor updates since then. It is published by the international organization for standardization (iso) and the international electrotechnical commission (iec) under the joint iso and iec subcommittee, iso/iec jtc 1/sc 27. Iso/iec 27001 specifies a management system that is intended to bring information security under management control and gives specific requirements. Organizations that meet the requirements may be certified by an accredited certification body following successful completion of an audit. Most organizations have a number of information security controls. However, without an information security management system (isms), controls tend to be somewhat disorganized and disjointed, having been implemented often as point solutions to specific situations or simply as a matter of convention. Security controls in operation typically address certain aspects of it or data security specifically; leaving non-it information assets (such as paperwork and proprietary knowledge) less protected on the whole. Moreover, business continuity planning and physical security may be managed quite independently of it or information security while human resources practices may make little reference to the need to define and assign information security roles and responsibilities throughout the organization.
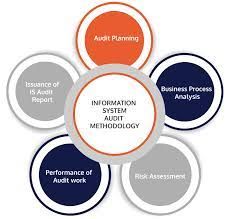
Information System Audits Service
Get Price Quote
An information systems audit performed by us is a comprehensive examination of a given targeted system. The audit consists of an evaluation of the components which comprise that system, with examination and testing in the following areas: High-level systems architecture review Business process mapping (e.g. determining information systems dependency with respect to user business processes) End user identity management (e.g. authentication mechanisms, password standards, roles limiting or granting systems functionality) Operating systems configurations (e.g. services hardening) Application security controls Database access controls (e.g. database configuration, account access to the database, roles defined in the database) Anti-virus/Anti-malware controls Network controls (e.g. running configurations on switches and routers, use of Access control lists, and firewall rules) Logging and auditing systems and processes IT privileged access control (e.g. System Administrator or root access) IT processes in support of the system (e.g. user account reviews, change management) Backup/Restore procedures
Looking for Information Systems Service Providers

geographical information system services
Get Price Quote
geographical information system services, Data Verification & QC

geographical information system
Get Price Quote
geographical information system

Integrated Retail Information System
Get Price Quote
Integrated Retail Information System, Facility Management Services