
Security Automation - SA
All types of business are slowly migrating towards automation. Advantages in terms of the quality of work, accuracy, readiness, efficiency, cost and effort. Identify and automate all your tedious security specific manual tasks with our customized automation service.
...more
pos machine
Type : Pos Machine
Color : Black, Blue, Cream, Grey, White
Voltage : 220V, 240V, 450V
Condition : New, Used
Driven Type : Battery Operated, Electric Operated
Feature : Durable, Fast Processor, High Speed, Low Consumption, Smooth Function, Stable Performance, Superior Work
Warranty : 1year, 2years, 3years
Connectivity : Wired, Wireless
...more
Vulnerability Management System
An enterprise cloud-based vulnerability management and reporting system. Organizations can install mars either on their own data centers or use our cloud hosting platform for access. This unique product combines various salient features keeping in mind the security functions carried out at an enterprise level.
...more
Credit Card Machine
Type : Credit Card Machine
Certification : CE Certified, ISO 9001:2008
Color : Black, Brown, Grey, Light White
Voltage : 110V, 220V, 380V, 440V
Condition : New, Used
Automatic Grade : Automatic
Driven Type : Electric, Hydraulic, Penaumatic
Warrenty : 1year, 2years
...more
Bullet Camera
Type : Bullet Camera, Digital Bullet Camera
Brand Name : CP Plus, Hk Vision, Honeywell, Samsung, Toshiba
Style : Bullet Camera
Certification : ISO 9001:2008 Certified
Application : Bank, College, Hospital, Restaurant, School, Station
Color : Black, Grey, White
Condition : New, Used
Driven : Electric
Warrenty : 1year, 2years
...more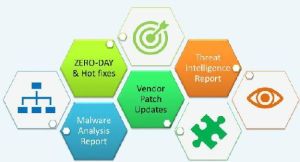
Threat Intelligence process
Hacking incidents such as the Ransomware attacks due to Phishing emails are on the rise. Threat Intelligence is the process of gathering, analyzing and providing the relevant Vendor patch updates hot fix details for the prevailing Threats. Staying up-to-date with the latest security threats, exploits, viruses, Trojans and malwares is very tedious activity for any Organization. Outsourcing this activity ensures your Organization stays updated.
...more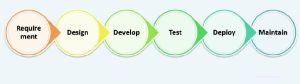
Software Development Services
Software applications have changed the way Business operates in our day-to-day life. Ever changing technology landscape keep us on our toes, exceeding Client expectations is a challenging task and is directly proportionate to getting more Business from the same Client. SDaaS ensures you get the best of your requirements with minimal time and cost.
...more
On-demand Security Training - OdST
Training programs speed-up the learning curve and assist your trainees to readily and efficiently excel in their given tasks. We provide information security specific trainings to your resourcesemployees at your premise. The program targets audience ranging from freshers to senior executives. We cover industry standards and compliance such as owasp, sans, pci-dss, pa dss, sox, etc. And even organization specific customized trainings.
...more
business continuity management services
Service availability is the most cruicial criteria for any Business to succeed. There are real-time security incidents of Clients losing their Business due to the Phishing emails, Social Engineering attacks, application downtime, Denial of Service (DOS), Distributed Denial of Service (DDOS) and many more hacking incidents. The main objective of BCMS is to ensure your Business runs smoothly with a minimum acceptable downtime.
...more
Annual Maintenance and Support - AMS
Confidentiality, Integrity, and Availability (CIA) which are the triage of Information Security is a critical aspect for any Business to run smoothly. Users expect the application to be available round the clock under all circumstances. Engage our services to get a vast range of IT Services, including Softwares, Computer peripherals to consumables that helps run your day-to-day Business.
...more
Centralized Reporting and Management

Security as a Service

Threat Modeling

web application security

Secure Code Review

Network Security

Vulnerability Assessment and Penetration Testing
Be first to Rate
Rate This