




Information Security Audit Service
Get Price Quote
An examination of the management controls within an Information technology (IT) infrastructure. The evaluation of obtained report determines if the information systems are protecting assets, maintaining data integrity, and operating effectively to achieve the organisation's goals or objectives. IT audit not only assess physical security controls, but also overall business and financial controls that involve information technology systems.
INFORMATION & CYBER SECURITY AUDITS :
Get Price Quote
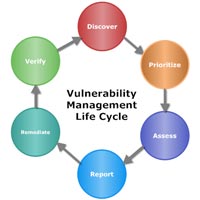
ISO / IEC 27001 : Information Security Management System (ISMS) : ISO standard audits in accordance with various scopes are conducted by organizations habitually. The standards enabling to secure and store any digital information are cited in 27001:2013, encouraging your organization to manage data pertaining to intellectual property, financial information, client information, employee records, etc. Also ensures a sustainability of processes, policies and several information security risk measures. Phases of an effective audit : Initiating the process by - Identifying the areas of focus along with documentation reviews (prior info sec audits conducted). Conceiving an audit plan specific to the client’s scope of business. Preparation involves a workable audit plan including the timing, required resources, charts / illustrations, checkpoints, laying boundaries specific to the required information concerned with the audit. Execution of the audit through gathering relevant information (system / network data, printouts, policy documentations, interviews with team members, etc) onsite. "Also involves gap analysis during specific audits". The entire gathered information is categorized individually and validated for its authenticity. Also identifying pain points in the system and assessing the requirement of further evaluation. Reporting - the most imperative aspect of an audit, this essentially contains A brief mention about the entire scope, objective, resources involved, and time taken for the entire exercise. limpse upon the key findings and their scope in audit. Detailed analytical description about the technical findings obtained from the audit. Conclusions and future recommendations. ·
Looking for Security Audit Service Providers

Security Audits Service
Get Price Quote
Security Audits Service, Servers Security Service, Employee Screening Service

Information Security Audit Service
Get Price Quote
Information Security Audit Service

Application Security Audits
Get Price Quote
Application Security Audits, Network Penetration Tests

Security Audits Services
Get Price Quote
Security Audits Services, Security Services

Information Systems & Security Audit
Get Price Quote
Information Systems & Security Audit

application security audit
Get Price Quote
application security audit, Application Security Audit Service

It Security Audit Services
Get Price Quote
It Security Audit Services, Security Configuration Management

Information Security Audits Services
Get Price Quote
Information Security Audits Services

information security audit
Get Price Quote
information security audit, application security

Security Analysis & Audit, Cyber Security and Consulting
Get Price Quote
Security Analysis & Audit, Cyber Security and Consulting, armed guards

Information Security Audits
Get Price Quote
Information Security Audits, Desktop, Network, Application And Server

IT Security Audits
Get Price Quote
IT Security Audits, IT Assessment, IS Training

security audit
Get Price Quote
security audit, supply chain management system, network designing services